[
Recently, a small number of iPhone users in 92 countries received an unexpected notification from Apple.
It was a stark warning that their devices might be under attack by mercenary spyware known for targeting specific individuals.
Threat notification from Apple. (Apple)
Apple’s warning: A call to vigilance
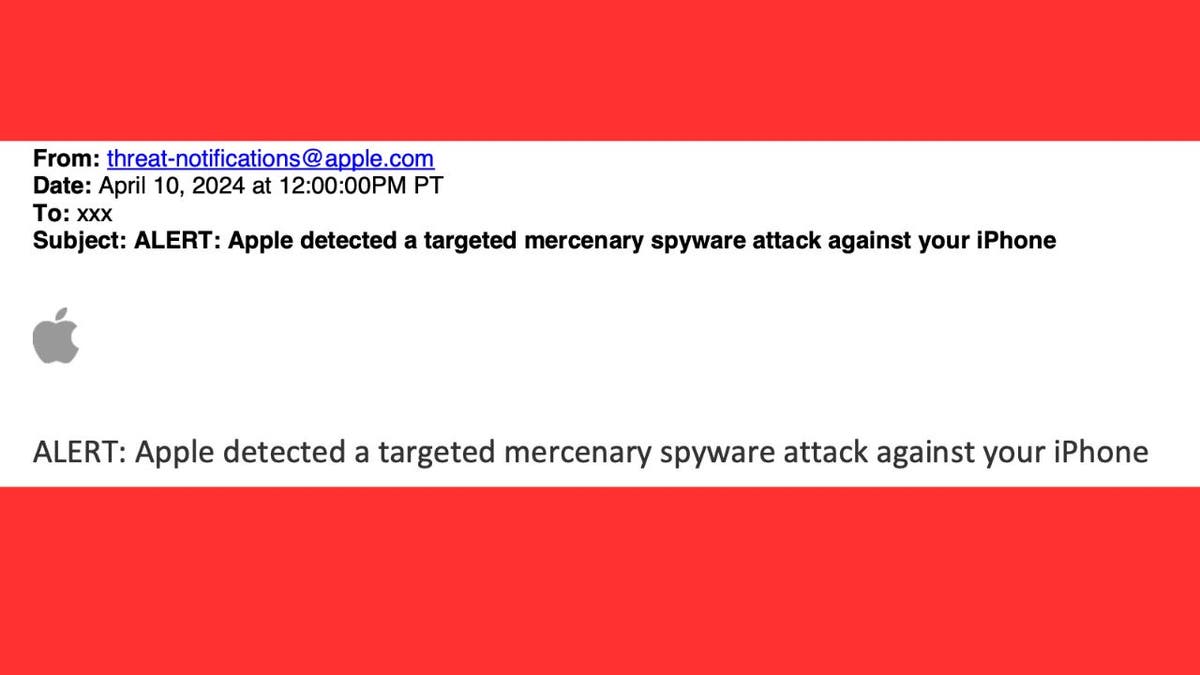
The notification was clear and alarming: “Apple detected a targeted mercenary spyware attack against your iPhone.” It urged users to take the threat seriously. When Apple identifies potential mercenary spyware activity, affected users are alerted through two distinct methods:
- Upon signing into appleid.apple.com, users will find a Threat Notification prominently displayed at the top of the webpage.
- Additionally, Apple dispatches notifications via email and iMessage directly to the contact details linked to the user’s Apple ID.
Since 2021, Apple has regularly notified individuals through this program.
Threat notification sent by Apple. (Apple)
MORE: CHANGE THIS APPLE MUSIC SETTING ASAP TO PROTECT YOUR PRIVACY
Understanding Apple’s alert protocol for spyware threats
Mercenary spyware attacks are sophisticated and continuously evolving, backed by substantial funding. Apple’s approach to identifying these threats is rooted in its proprietary threat intelligence and investigative processes.
While absolute certainty in detection is unattainable, Apple’s threat notifications carry a high degree of confidence. They indicate that an individual has been specifically targeted by such an attack and warrants serious attention.
Apple does not disclose the specific triggers for these alerts to maintain the integrity of detection methods and prevent attackers from modifying their tactics.

iPhone and Mac. (Kurt “CyberGuy” Knutsson)
MORE: APPLE IS FIGHTING BACK AGAINST QUANTUM ATTACKS WITH NEW SECURITY SYSTEM FOR IMESSAGE
How to verify authentic threat notifications
It’s important to note that genuine Apple threat notifications will never solicit actions such as clicking links, downloading files, installing apps or profiles, or sharing your Apple ID credentials. The authenticity of a threat notification can be confirmed by signing into appleid.apple.com, where any legitimate alerts will be prominently displayed after login.

Woman holding iPhone. (Kurt “CyberGuy” Knutsson)
POLAND’S PROSECUTOR GENERAL SAYS PREVIOUS GOVERNMENT USED POWERFUL SPYWARE AGAINST HUNDREDS
Next steps after receiving an Apple threat notification
If you receive an Apple threat notification, it is imperative to seek specialized assistance. The Digital Security Helpline by Access Now offers rapid-response emergency security support and is accessible 24/7 via its website. While external organizations are not privy to the reasons behind Apple’s issuance of a threat notification, they are equipped to provide personalized security guidance to those affected.

Woman on iPhone. (Kurt “CyberGuy” Knutsson)
Best security practices for all Apple users
By following these essential security practices, you can protect yourself against ever-evolving cyber threats.
1. Stay ahead of the game: Always update your devices to the latest software version to ensure you have the most recent security updates.
2. Lock it up tight: Secure your devices with a passcode to prevent unauthorized access.
3. Double the defense: Enable two-factor authentication and use a strong password for your Apple ID to enhance account security.
GET FOX BUSINESS ON THE GO BY CLICKING HERE
4. Safe downloads only: Only install apps from the official App Store to avoid malicious software.
5. Password power play: To protect your personal information, create strong and unique passwords for your online accounts. Consider using a password manager to generate and store complex passwords.
6. Think before you click: Avoid clicking on links or downloading attachments from unknown sources to prevent potential security breaches. The best way to protect yourself from clicking malicious links that install malware that may get access to your private information is to have antivirus protection installed on all your devices. This can also alert you of any phishing emails or ransomware scams.
For those who have not received a threat notification but suspect they might be targets of mercenary spyware, Apple’s Lockdown Mode offers an additional layer of protection.
MORE: APPLE CRACKS DOWN ON IPHONE THIEVES WITH NEW SECURITY SETTING
Kurt’s key takeaways
The recent spyware alerts from Apple serve as a stark reminder of the evolving landscape of digital threats. Apple’s Lockdown Mode and the company’s commitment to notifying affected users reflect a dedication to security in an age where cyber warfare is becoming increasingly personalized. As we navigate this digital battlefield, staying informed and prepared is our best defense.
CLICK HERE TO GET THE FOX NEWS APP
What measures should tech companies like Apple take to protect you from advanced mercenary spyware further? Let us know by writing us at Cyberguy.com/Contact
For more of my tech tips & security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter
Ask Kurt a question or let us know what stories you’d like us to cover.
Answers to the most-asked CyberGuy questions:
Copyright 2024 CyberGuy.com. All rights reserved.







